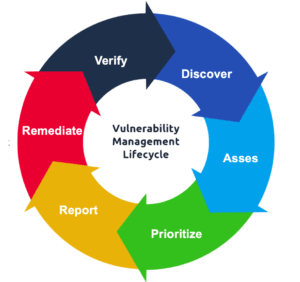
What is vulnerability management?
Vulnerability management (VM) is the process of identifying, evaluating, treating, and reporting on security vulnerabilities in systems and the software that runs on those systems. A VM program is crucial for organizations that wish to prioritize possible threats and minimize their attack surfaces.
Vulnerabilities are essentially technological weaknesses that allow attackers to compromise a product and the information it holds. Continuous VM is necessary as new systems are added to networks and as changes are made to those systems. Vulnerability scans lie at the heart of a solid VM program, with the United States Cybersecurity and Infrastructure Agency (CISA) even offering scans as a standard component of a partnered VM service with the Department of Justice.
What is risk based vulnerability management?
Risk-based vulnerability management (RBVM) is a modern approach to prioritizing and addressing vulnerabilities based on the specific risks they pose to an organization. Unlike traditional vulnerability management – which often focuses on the sheer number of vulnerabilities – RBVM goes further by incorporating additional context, such as asset criticality, exploitability, and real-world threat intelligence.
At its core, RBVM evaluates vulnerabilities not in isolation but as part of a broader risk profile. It emphasizes the importance of aligning remediation efforts with the organization’s risk tolerance, business objectives, and overall security posture. By prioritizing vulnerabilities based on their actual risk rather than theoretical severity, organizations can better protect critical systems and data.
If you would like to engage us for any of the above service, Contact us

